11 | Add to Reading ListSource URL: eprint.iacr.orgLanguage: English - Date: 2006-12-21 12:10:24
|
|---|
12 | Add to Reading ListSource URL: www.cis.upenn.eduLanguage: English - Date: 2014-11-18 15:19:13
|
|---|
13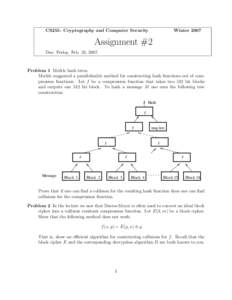 | Add to Reading ListSource URL: crypto.stanford.eduLanguage: English - Date: 2007-02-17 22:43:38
|
|---|
14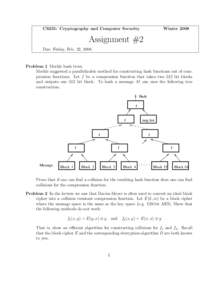 | Add to Reading ListSource URL: crypto.stanford.eduLanguage: English - Date: 2008-02-20 19:40:28
|
|---|
15 | Add to Reading ListSource URL: eprint.iacr.orgLanguage: English - Date: 2008-08-25 02:24:24
|
|---|
16 | Add to Reading ListSource URL: eprint.iacr.orgLanguage: English - Date: 2010-08-04 14:03:01
|
|---|
17 | Add to Reading ListSource URL: csrc.nist.govLanguage: English |
|---|
18 | Add to Reading ListSource URL: antoine.delignat-lavaud.frLanguage: English - Date: 2010-08-17 15:48:58
|
|---|
19 | Add to Reading ListSource URL: csrc.nist.govLanguage: English - Date: 2014-08-22 14:11:37
|
|---|
20 | Add to Reading ListSource URL: www.iacr.orgLanguage: English - Date: 2009-03-05 01:27:34
|
|---|